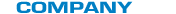- Vicomsoft and your network security
-
InterGate Policy Manager for Mac OS X and InterGate Policy Manager for Windows, provides you with a set of network security and monitoring tools that keep your organization and your users safe from a wide array of Internet threats. That is a fairly broad statement so before we examine what InterGate Policy Manager does, let's make sure we agree on what those threats are.
- Spam emails pose the risk of lost productivity when deleting them, infecting
the network with viruses from incoming emails and infecting other networks
from viruses in outbound emails with the accompanying embarrassment and potential
legal liability.
- Personal surfing poses the risk of lost productivity, legal liability and malware installed on the network with the associated risk of breach of confidentiality.
- File sharing poses the risk of exposing confidential information to unknown parties.
- Instant messaging allows users to transmit information undetected, and effectively
punches a hole in the firewall, potentially exposing the client machine to
unauthorized access through security vulnerabilities in the IM application
itself.
- Internet telephony uses your bandwidth for other people's needs.
In all of the above areas, your users may expose themselves and your organization to financial or legal harm without malice and without even knowing they are doing it. User awareness is important, but alone will not avert disaster. Simply put, you need tools to ensure that you are safe. You may know and obey the rules of the road, but without a seatbelt you are not safe.
InterGate Policy Manager provides you with the ability to monitor, report and optionally block all of the above types of Internet traffic on a highly selective and granular level. Furthermore, the number and type of threats it protects you from is constantly being updated automatically without any intervention on your part.
- Predefined Web Filters:
- We licence SurfControl's database of over 13 million sites covering 2 billion
web pages and 40 well-organized categories, which are updated on a daily
basis. No single solution will fit all networks. Concerns range from protecting
minors to maintaining productivity. In using SurfControl's industry-standard
40 web surfing categories to choose from, you acquire the ability to finely
tune your organization's Internet acceptable use. There is no point in spending
time defining what is acceptable only to find that the tools you plan to
use do not allow you to differentiate between safe and unsafe access.
- SafeSearch:
- The major search engines have an Advanced Search feature
giving you the option for "No Filter" or "Filter using SafeSearch". Without
InterGate Inspect from Vicomsoft, it is a simple matter for the user to
switch between the two options at will. InterGate Inspect gives you the
flexibility to enforce the SafeSearch option.
- User-defined Web Filters:
- In addition to SurfControl's database, you can define your own exception list which overrides the main database. This can allow denied sites or deny allowed sites. It basically puts you in complete control.
- Application Filters:
- These block or allow Peer-to-Peer applications such as AIM (AOL Instant Messenger), ICQ, Yahoo Messenger, MSN Messenger, eDonkey, eMule, Kademlia, BitTorrent, Gnutella (Morpheus, LimeWire), Kazaa, Skype. You may not fully appreciate what is involved here, so a short technical explanation is in order. The Internet runs on a set of protocols. They are too numerous to mention here, but they include HyperText Transfer Protocol (HTTP), Post Office Protocol (POP), and Simple Mail Transfer Protocol (SMTP) which are more or less the backbone of Internet traffic, and you likely use all three of these every day. There are, however quite a number of additional protocols like Internet Relay Chat (IRC) that are widely used, although not fundamentally needed by most people on a day-to-day basis on the job. Now when two computers are sending traffic back and forth using one of these protocols, they generally assign a port number, which is just a number from 1 to 32000 to help keep things tidy when sorting out the packets. Routers and applications like browsers are aware of these port number, but users rarely are. Port numbers are usually always the same for any given protocol. For example, HTTP generally uses port 80, while IRC uses port 194. Why do you need to know all this? Well, there are three ways to control or block a protocol such as IRC. One is to block access to a web site that does it. This has the disadvantage of blocking access to other potentially useful parts of the same web site, while requiring you to know the address of every IRC web site in the world. The second way is to block port 194. This is unsafe, because the use of port 194 is a convention, not a requirement. You can send IRC through any port. The best and safest way to block a protocol is to recognize it by examining the packet headers as they are routed to and from the Internet and positively identify IRC or any other packets. This is what InterGate Policy Manager Application Filters do.
- Skype Filtering:
- This is one of InterGate's Application Filters mentioned above. It is being dealt with specifically here because it is becoming extremely popular, and few users are aware of the issues. InterGate filters it on a per user, per group or per machine basis. Skype is one of the hottest and most disruptive technologies to emerge in some time. Skype simply allows you to make free telephone calls over the Internet anywhere in the world. This has the telcos worried, but the users love it. It is a potential boon to businesses that need to keep constant contact with personnel or business partners abroad. The benefits to your organization could be enormous, on the condition that you implement it in a way that manages the risk. And the only way to do that is to know exactly who is using Skype, when they are using it, and to allow only safe access by authorized users. InterGate Policy Manager empowers you to do this.
- Protocol Filters:
- These block or allow specific types of traffic such as FTP, POP3, HTTP. These protocols generally use fixed port numbers that were assigned to them when when the protocols were first introduced. Protocol filters simply block the well-known port number associated with the protocol. This is simple, effective and quite sufficient, say, for preventing a user from fetching email from a server outside the local area network. For more subtle threats, we recommend the use of Application Filters.
- Time controls:
- Although we provide you with tools of the trade, it is up to you to decide what to do with them. We don't want to force you to be heavy-handed in your approach. If users are allowed to do personal shopping on the Internet outside of work hours, you can enable this because of time controls. On the other hand, you could prevent any access at all outside certain hours. It's up to you.
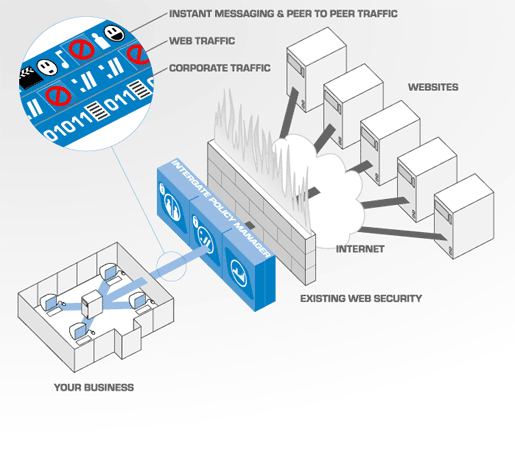
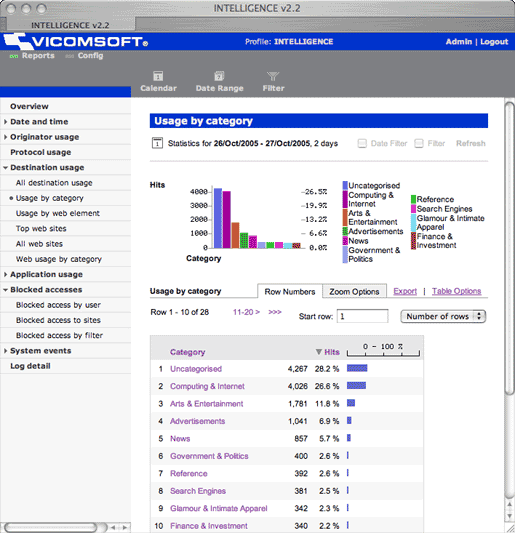
- Flexible Reporting:
- Summary and drill-down reports on Internet usage including access or attempted access by category of site, protocol, user, group, machine and time of day can be produced with a few clicks by anyone with the necessary access privileges. Remember, a breach of security is nearly always preceded by a breach of policy. Knowing what is going on is indispensable. Many of our customers are utterly amazed when they get a grip on what kind of traffic is actually going over their network. It is one thing to know the number of attempts at accessing unauthorized sites. It is another to know when the attempts are occurring and where they are coming from.
- Email Threat Management:
-
This managed service offers protection with 98% spam detection rates, 100% protection from email borne viruses, protection from "denial of service" attacks, email archiving to ensure regulatory compliance. It is a fully managed 24/7 service, hosted on the Internet and requiring limited or no IT maintenance and no software or hardware to be installed, configured or maintained. Emails are scanned and processed in accordance with the user's spam policy which may be modified to suit the organization's overall security policy.
- Subscription Based Solution:
-
As we mention, often network security is a moving target. You need to partner
with someone who eats, sleeps and breathes security. InterGate Policy Manager
modules are available on a subscription basis. You get regular updates, without
having to go through the process of a buying decision and procurement. The
database of web sites is updated every day. Other services such as protocol
management are updated as soon as new threat patterns emerge. Email spam and
virus controls are offered as a managed service, so you need to do absolutely
nothing to stay ahead of current threats. You may wish to keep abreast of these
developments, but if your primary responsibilities in your organization keep
you away from the security front for days at a time, you can rest assured that
your security updates will continue.
|



 Features
Features